Triage AWS RDS DB Instances should have deletion protection enabled ENHANCED_MONITORING_NOT_ENABLED
Quick Links
- Configure AWS RDS DB Instances should have deletion protection enabled
- Use Case for AWS RDS DB Instances should have deletion protection enabled
- Triage Guides by Violation Type
Why should I care about fixing this issue?
To get started on understanding RDS Enhanced Monitoring, read our use-case page.
What is the data source for this policy?
This policy relies on a call to rds:DescribeDBInstances. If the response of the property EnhancedMonitoringResourceArn is present, then a violation is opened by the policy.
Does this policy scan on a schedule? If so, when?
No, it's triggered when changes to matching resources are detected.
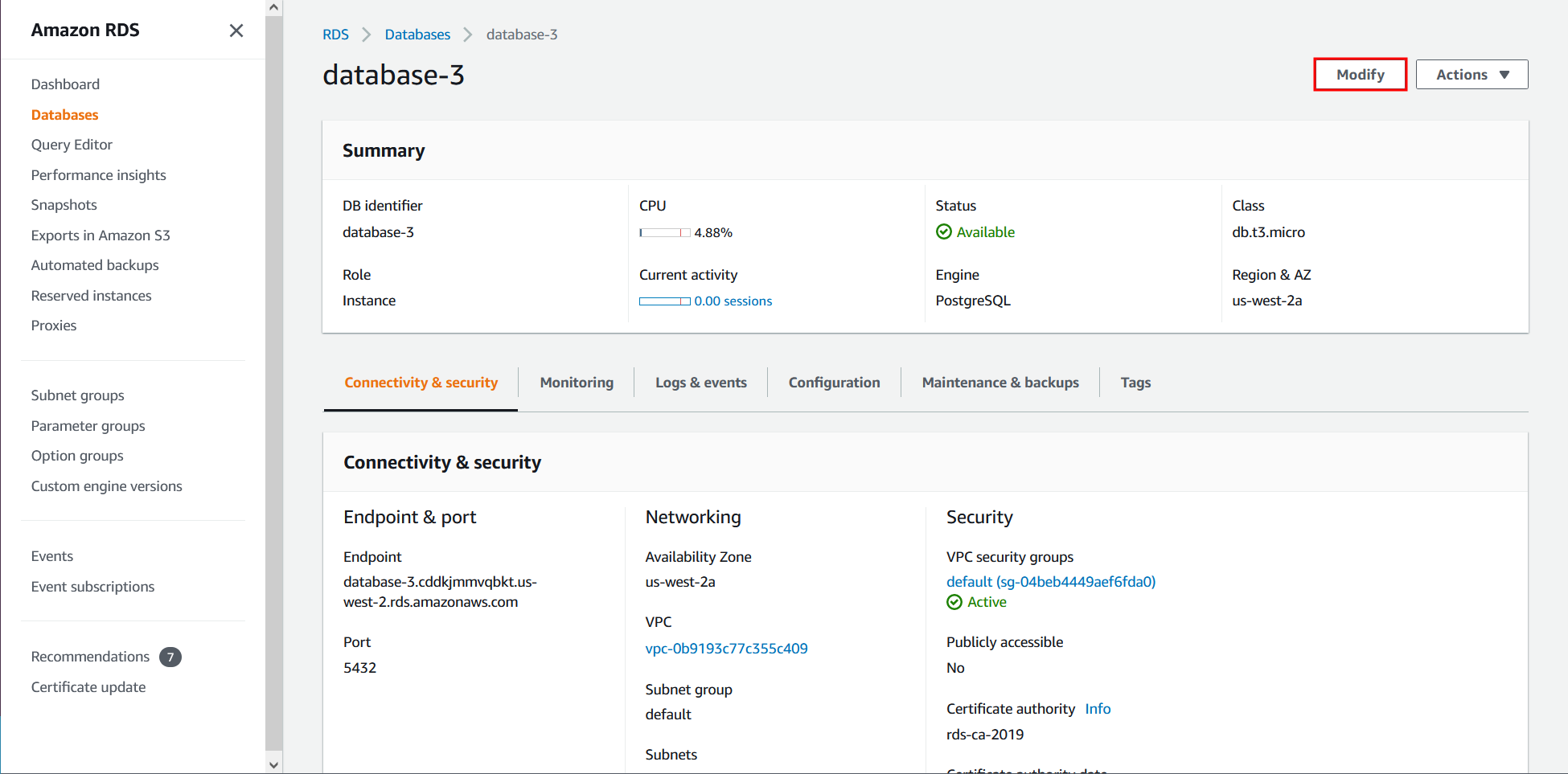
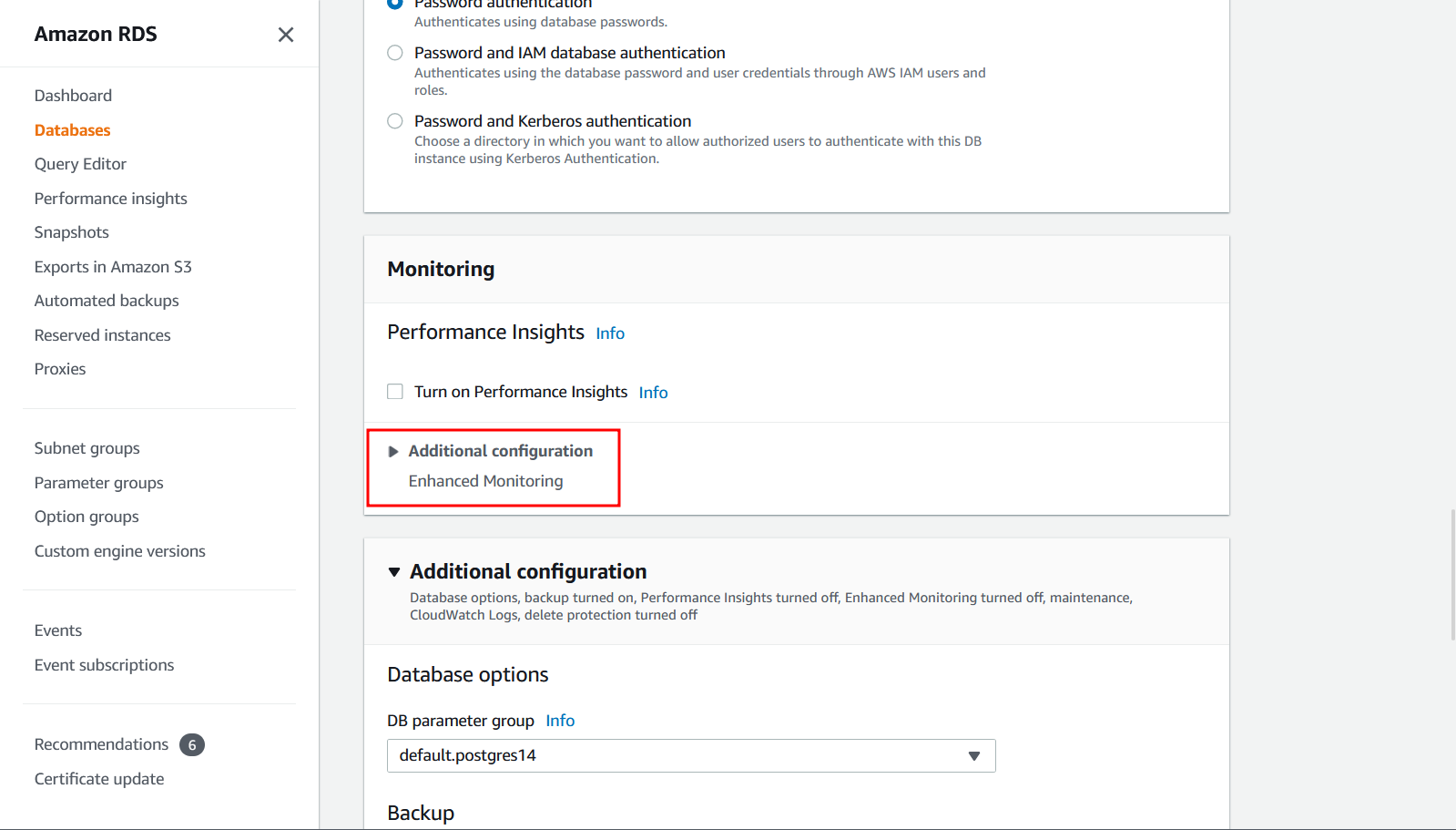
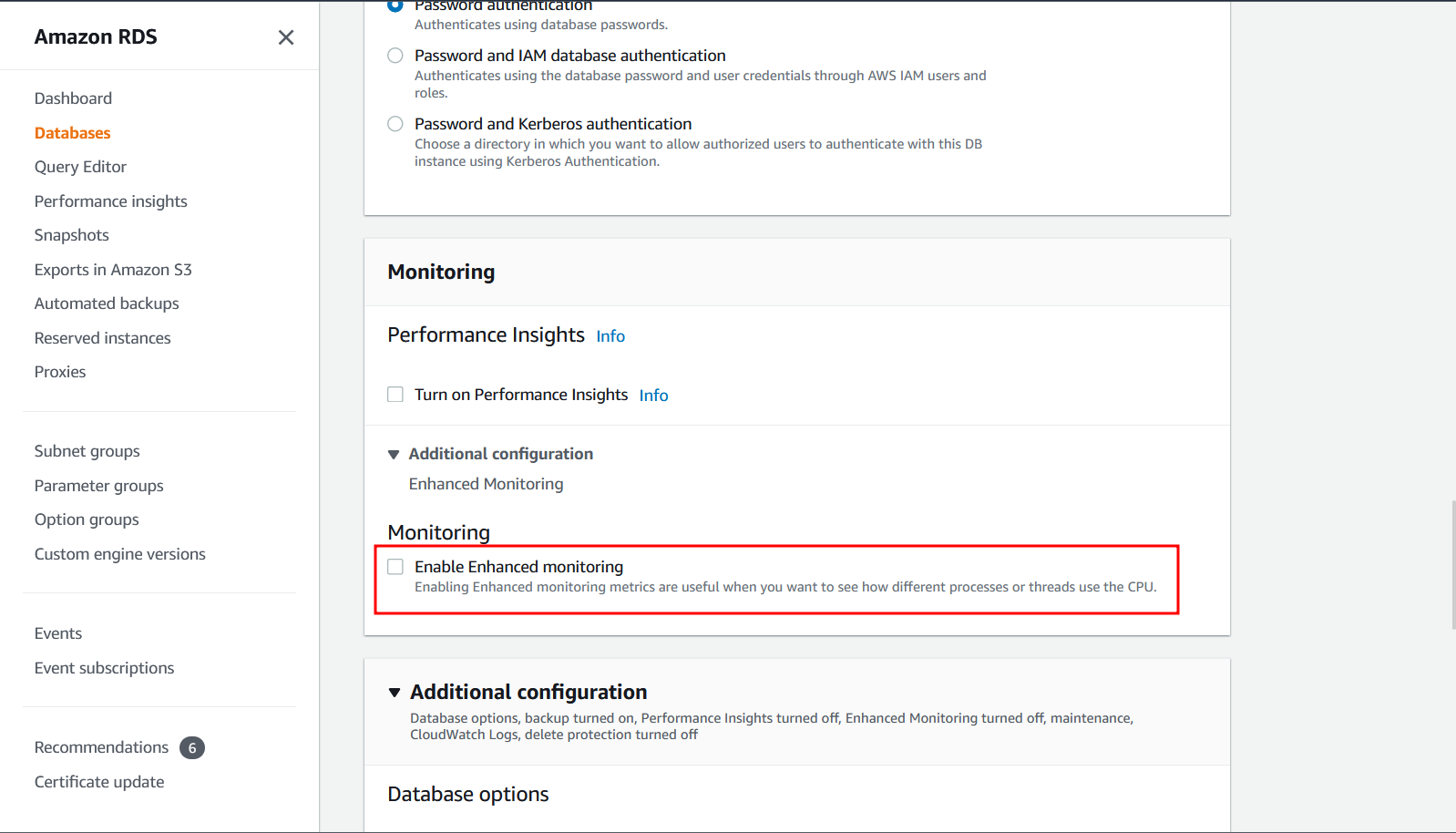
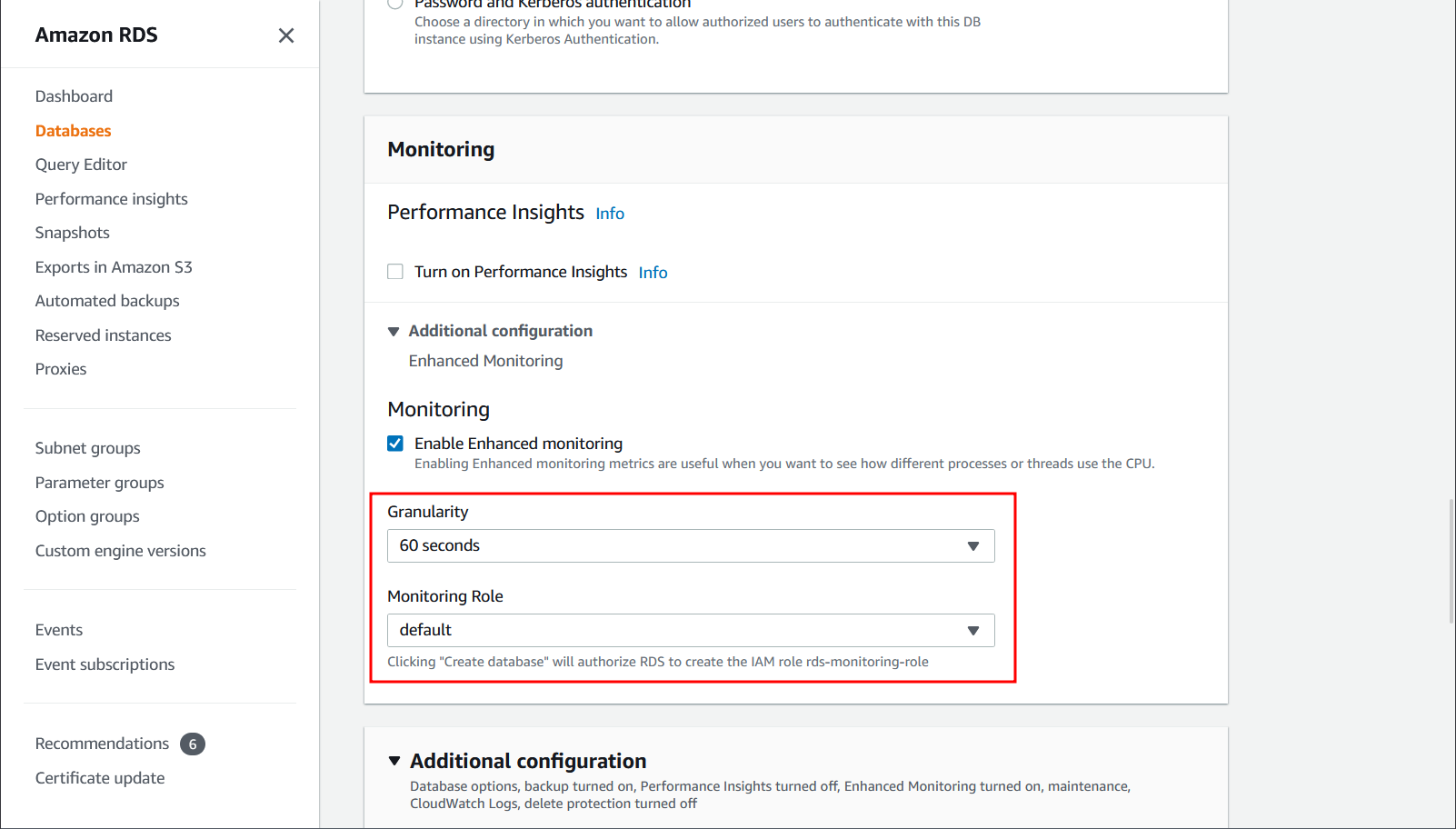
How do I enable enhanced monitoring using AWS Console?
See the console instructions on Turning Enhanced Monitoring on and off.
How do I enable enhanced monitoring using CloudFormation?
- Create an AWS::IAM::Role and attach the AmazonRDSEnhancedMonitoringRole managed policy with the trusted entity set to the AWS service 'monitoring.rds.amazonaws.com'.
- On the AWS::RDS::DBInstance set MonitoringRoleArn to the created role's ARN.
- On the AWS::RDS::DBInstance set MonitoringInterval to the desired monitoring interval in seconds.
Here is a CloudFormation template example:
RDSMonitoringRole:
Type: AWS::IAM::Role
Properties:
ManagedPolicyArns:
- 'arn:aws:iam::aws:policy/service-role/AmazonRDSEnhancedMonitoringRole'
AssumeRolePolicyDocument:
Version: '2012-10-17'
Statement:
- Effect: Allow
Principal:
Service: 'monitoring.rds.amazonaws.com'
Action: 'sts:AssumeRole'
ExampleDBInstance:
Type: AWS::RDS::DBInstance
Properties:
MonitoringRoleArn: !GetAtt 'RDSMonitoringRole.Arn'
MonitoringInterval: 1
How do I enable enhanced monitoring using Terraform?
To enable Enhanced Monitoring with Terraform you need to set monitoring_role_arn and monitoring_interval on your aws_db_instance.
See the reference implementation for example IAM Role to use for the monitoring role.
How do I enable enhanced monitoring using AWS CLI?
See the CLI instructions on Turning Enhanced Monitoring on and off.
When is it appropriate to mark this violation as "by design"?
To get started on understanding RDS Enhanced Monitoring, read our use-case page.