Triage AWS RDS DB Instances should have deletion protection enabled DELETION_PROTECTION_NOT_ENABLED
Quick Links
- Configure AWS RDS DB Instances should have deletion protection enabled
- Use Case for AWS RDS DB Instances should have deletion protection enabled
- Triage Guides by Violation Type
Why should I care about fixing this issue?
To get started on understanding RDS Deletion Protection, read our use-case page.
What is the data source for this policy?
This policy relies on a call to rds:DescribeDBInstances. If the response of the property DeletionProtection is not true, then a violation is opened by the policy.
Does this policy scan on a schedule? If so, when?
No, it's triggered when changes to matching resources are detected.
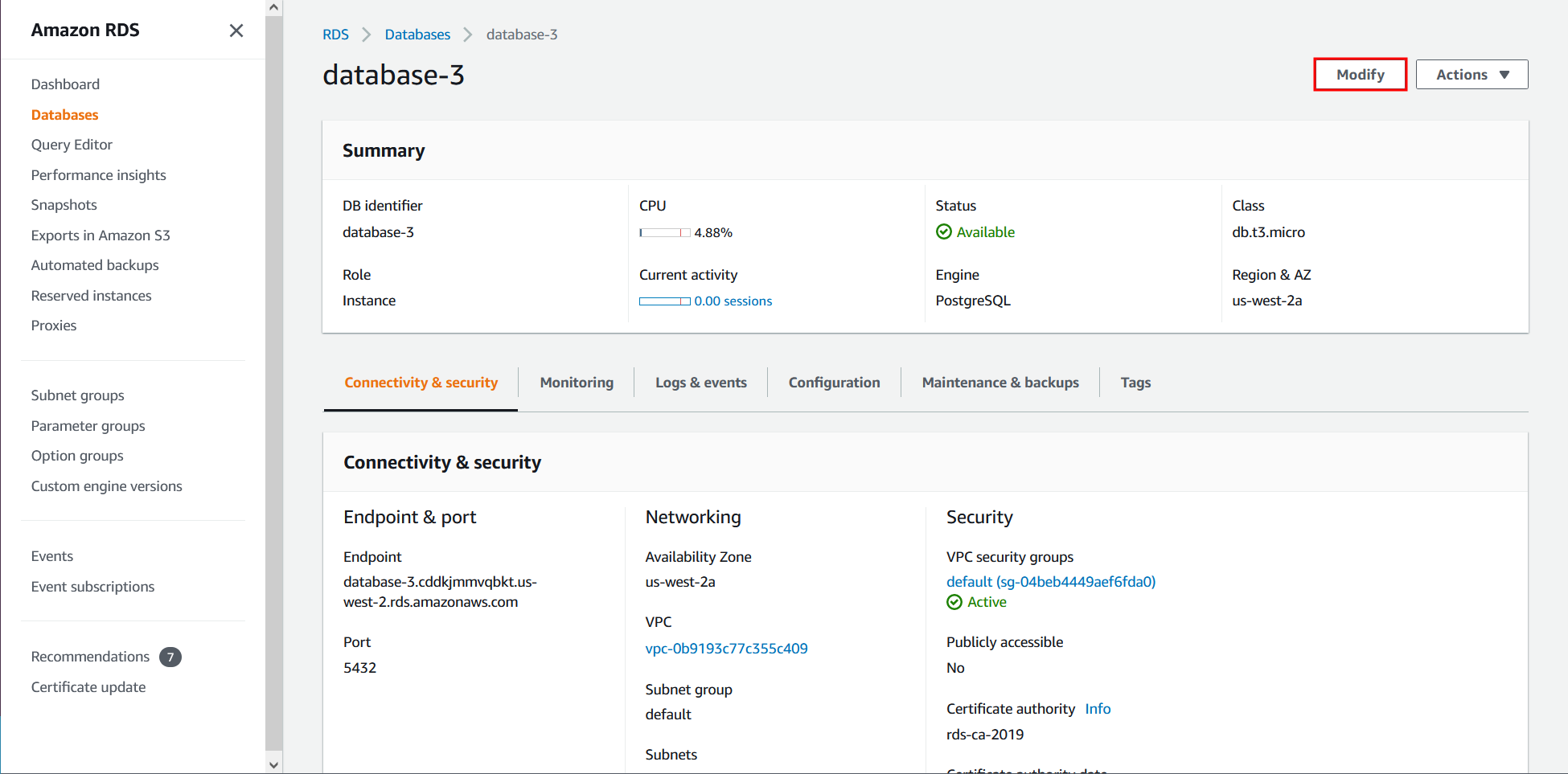
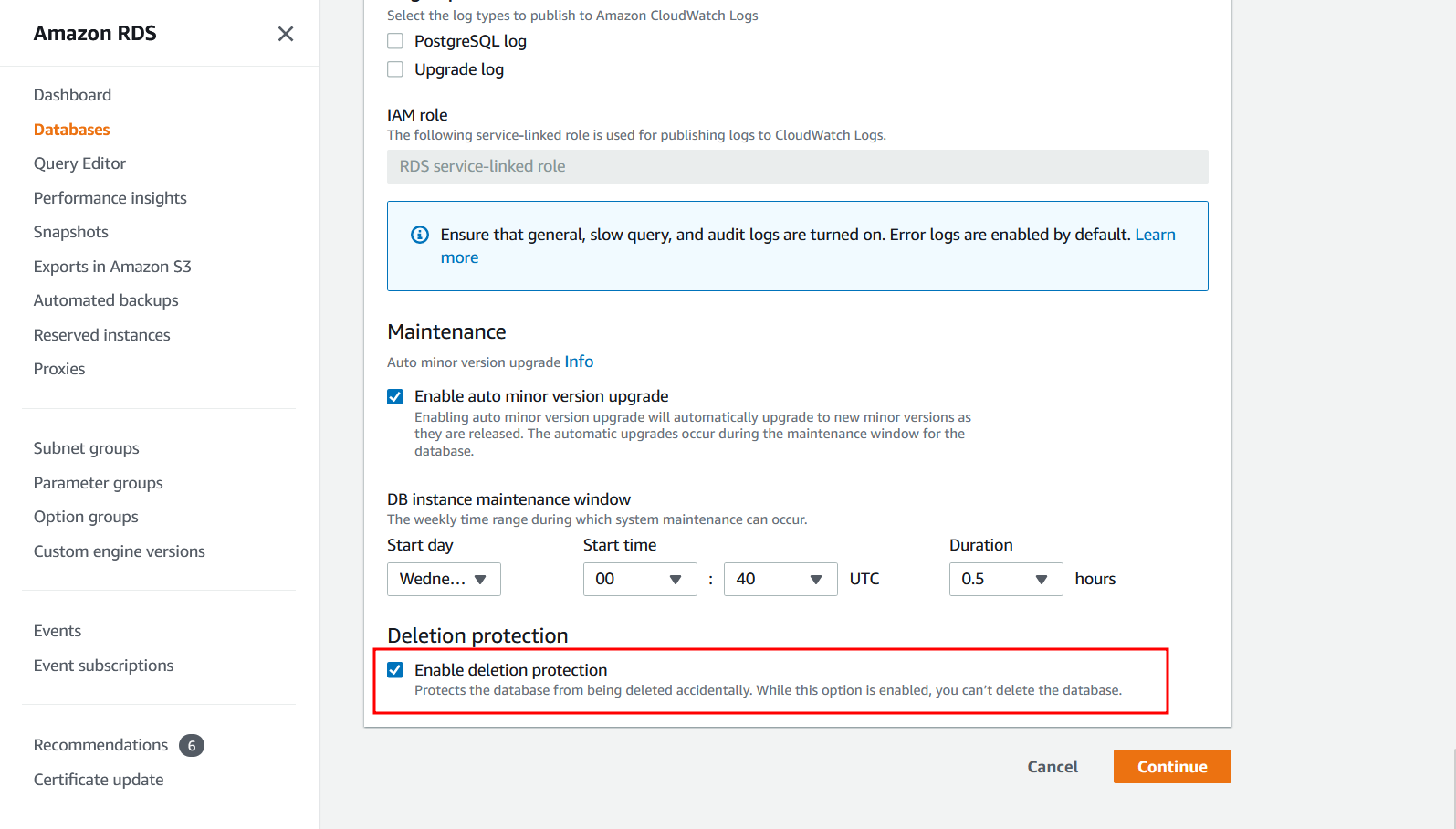
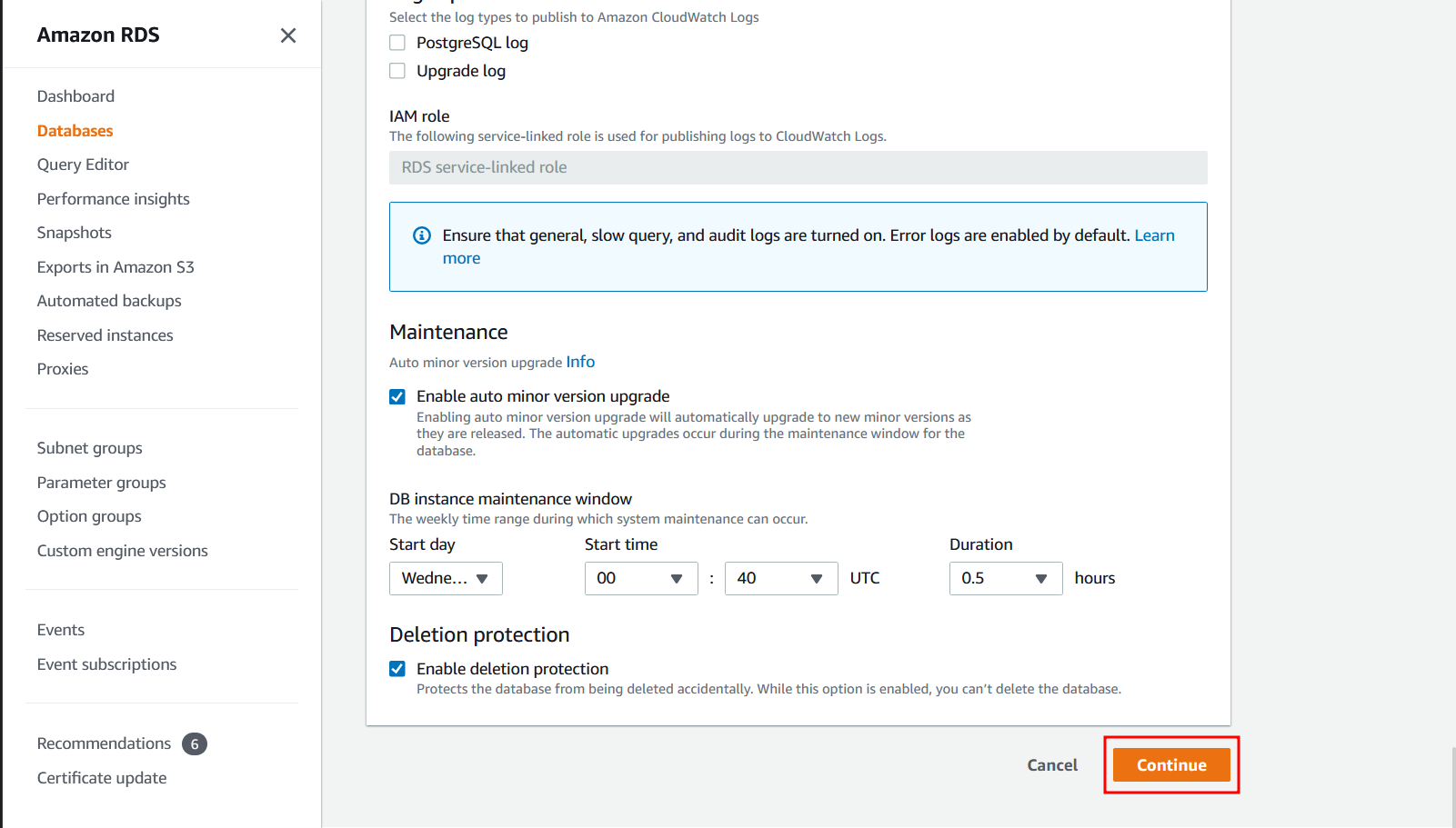
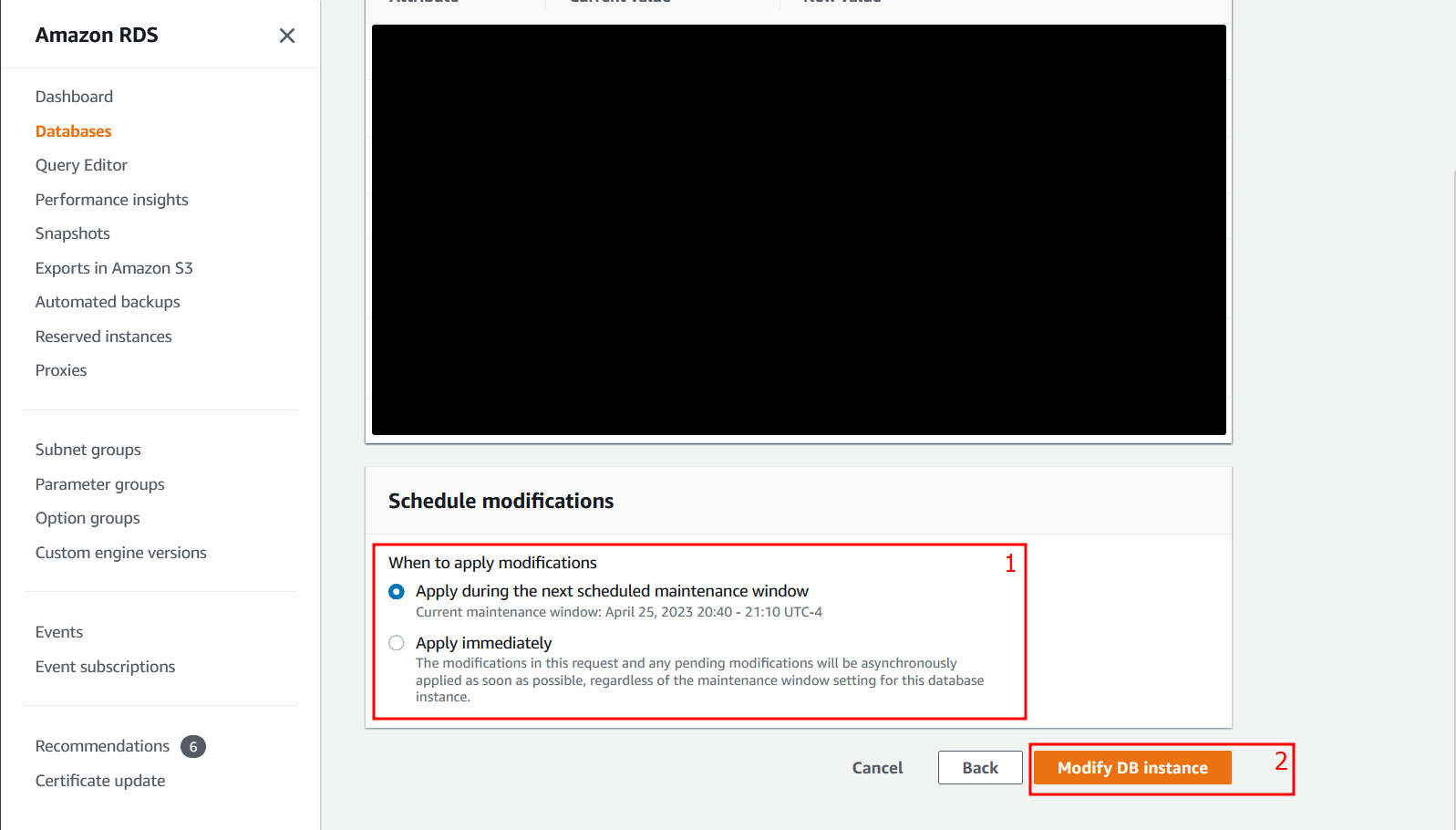
How do I enable deletion protection using AWS Console?
See the console instructions on Prerequisites for deleting a DB instance.
How do I enable deletion protection using CloudFormation?
Note that the field is not required and the default value is false.
Type: AWS::RDS::DBInstance
Properties:
- DeletionProtection: false
+ DeletionProtection: true
How do I enable deletion protection using Terraform?
Note that the field is not required, may not be present, and the default value is false (deletion protection disabled).
resource "aws_db_instance" "example" {
- auto_minor_version_upgrade = false
+ auto_minor_version_upgrade = true
}
How do I enable deletion protection using AWS CLI?
aws \
rds modify-db-instance \
--db-instance-identifier database-1 \
+ --deletion-protection
When is it appropriate to mark this violation as "by design"?
To get started on understanding RDS Deletion Protection, read our use-case page.